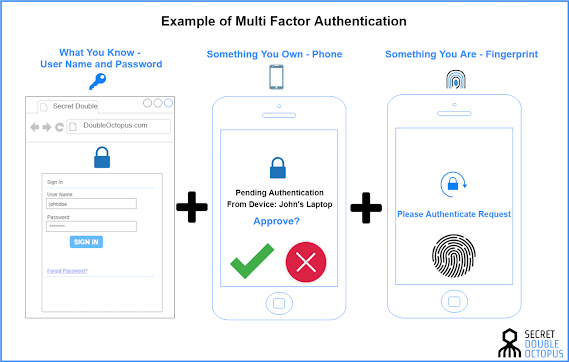
Grasping Alec Kassir's Perspective on Protecting Critical Infrastructure

Businesses confront formerly unheard-of hazards within the globally connected world, especially cyber threats. Renowned cybersecurity expert Alec Kassir stresses safeguarding crucial infrastructure, mainly in busy centers like Miami. Well, what does this imply? Grasping Alec Kassir's Perspective on Protecting Critical Infrastructure What Is the Protection of Critical Infrastructure? Protection of vital infrastructure includes defending vital structures against cyberattacks that could cause provider disruption. In addition to warding off attacks, Alec Kassir Miami emphasizes the significance of effectively responding to them when they do occur. Setoff and proportionate measures are vital to reduce harm and return to regular operations. The Definition of Critical Infrastructure Systems and networks that deliver essential services like electricity, telecommunications, banking, and healthcare are taken into consideration essential infrastructures. For present-day society to be charac...